Cyber attacks are becoming increasingly common and sophisticated, putting individuals, businesses, and governments at risk. It is crucial for us to understand the different types of cyber-attacks and the methods we can use to protect our systems. Before we jump into how to prevent or protect our system from cyber attacks we need to know the risk and common sources of cyber attacks in 2023.
Phishing Attacks
Phishing attacks are one of the most common types of cyber attacks. They are often used to steal personal and financial information such as passwords and credit card numbers. These attacks can be in the form of an email, message, or website that appears to be from a trusted source but is actually a fake. Phishing attacks can also be delivered through malicious links or attachments.
Ransomware Attacks
Ransomware attacks are a type of cyber attack in which an attacker encrypts the victim’s data and demands a ransom payment in exchange for the decryption key. This type of attack can be particularly devastating for businesses as it can result in the loss of sensitive data and disruption of operations. To know more about ransomware and tactics to prevent the attacks, learn from this article: A ransomware attack
Distributed Denial of Service (DDoS) Attacks
A DDoS attack is a type of cyber attack that involves overwhelming a website or network with a large amount of traffic. The goal of a DDoS attack is to make the targeted website or network unavailable to its users. This type of attack can be particularly damaging to businesses as it can result in loss of revenue and damage to reputation.
Malware Attacks

Malware is short for malicious software and refers to any program or code that is designed to cause harm to a computer system. This can include viruses, worms, Trojans and spyware. Malware attacks can cause a variety of problems, from stealing personal information to disrupting system functionality.
SQL Injection Attacks
SQL injection attacks are a type of cyber attack that target databases. The attacker is able to inject malicious code into the database to steal sensitive information, alter data or take control of the database. SQL injection attacks are particularly dangerous as they can result in widespread damage.
Man-in-the-Middle (MitM) Attacks
A Man-in-the-Middle attack is a type of cyber attack in which an attacker intercepts communications between two parties. The attacker is able to eavesdrop on the communications and even modify the data being exchanged. This type of attack can be particularly dangerous as it can result in the theft of sensitive information or the dissemination of false information.
Tactics to protect yourself from Cyber Attacks
To protect ourselves from these types of cyber attacks, it is important to take a multi-layered approach. This includes implementing the following measures:
Use Strong Passwords to prevent Cyberattacks
It is important to use strong and unique passwords for all of our online accounts. This makes it more difficult for attackers to gain access to our systems and personal information.
Keep Software Up to Date
Keeping software up to date is important as it helps to close any security vulnerabilities that may have been discovered. This includes operating systems, web browsers and applications.
Use Antivirus Software

Antivirus software can help to protect our systems from malware attacks. This software uses signature-based detection and behavior-based detection to identify and remove malicious software. To know about how to protect your company from cyber attacks, check out this article 🙂 Cyber attacks protection
Enable Firewall to prevent Cyberattacks
A firewall can help to protect our systems by blocking unauthorized access and controlling the flow of incoming and outgoing network traffic.It acts as a barrier between the internal network and the outside world, protecting against unauthorized access, malware, and other threats.
To know more about firewalls click on the link: Firewall for office
Enable Two-Factor Authentication
Enable Two-Factor Authentication Two-factor authentication provides an extra layer of security by requiring a second factor, such as a code sent to a phone, in addition to a password. This makes it more difficult for attackers to gain access to our systems. Apart from two-factor or multi-factor authentication, magic links can be used for safe login and eliminate the need to remember passwords.
Want to know how magic links work?
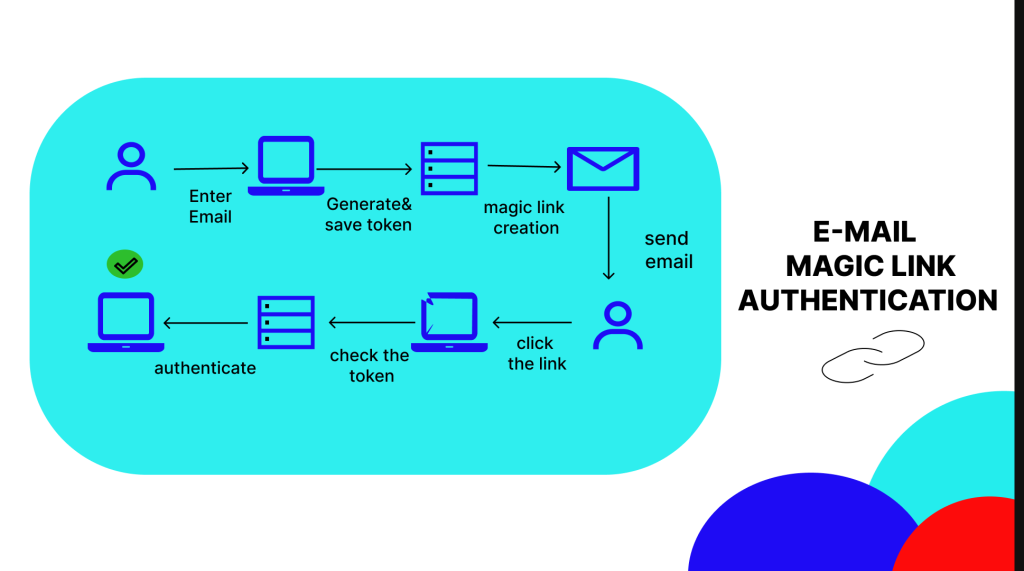
Backup data regularly
Backing up data regularly can help to protect against data loss in the event of a cyber attack. Here are some backup data options:
- External hard drive.
- Hardware appliances.
- Backup software.
- Cloud backup services.
For a free consultation for IT security service in your company contact us anytime – contact@invitty.com or WhatsApp or call : 8939335551
Willkommen im deutschen Online-Shop für hochwertige Replica-Uhren, um die besten Replik-Uhren in Deutschland zu kaufen.
